I haven't posted for a while as I try to stick to my mantra of only posting things that I have not yet been able to find on the internet. With that in mind I have been receiving a lot of requests from clients who want to use PCNS to synchronize passwords between two forests using selective authentication. I searched the internet for days trying to find any indication that this was possible, but without any luck. I decided to see if it was possible. I spent quite a bit of time working through the permissions needed and how best they could be implemented.
The good news is ... it is possible, reasonably simple and below I will show you how it's done.
First let me explain what the difference is between domain-wide and selective authentication.
· With Domain-wide authentication users from the trusted domains will automatically have access to the resources in the trusting domain.
· With Selective authentication users from the trusted domain need to be granted the specific rights to access resources in the trusting domain. This means that Selective Authentication is much more secure than domain-wide authentication, but also needs permissions to be explicitly granted to the relevant resources that access is required for.
What you will need:
- A one way external/forest trust with the forest/domain running PCNS needs to be trusted by the forest/domain running, My setup it looks as follows:

- PCNS Installed and configured on the domain controllers running in the trusted domain.
- Relevant frewall rules in place to allow PCNS traffic between the trusted and trusting domain.
- On Windows 2012 you will need to initially setup the trust as domain-wide in order to setup the permissions. Once they are configured you can change the trust back to selective authentication. On Windows 2008 it will prompt you to authenticate in order to assign the permissions.
- Name resolution working between the two forests. This can either be via conditional forwarders or by creating a secondary zone for each forest on the opposing forest. I would suggest that you limit the amount of DC’s that can be resolved for the trusting domain as you will need to grant permissions to each domain controller that can be resolved in the trusted domain via DNS.
- Domain Admin access to the trusting domain in order to assign the permissions and change the required group policies.
- Domain Admin access to the trusted domain to lookup user and computer object in the trusted domain and change the required group policies.
- You will notice that I use the domain controllers group in place of the machine accounts of the domain controllers for obvious reasons.
How it is done:
1. Trust
a. Setup the trust as specified.
2. Trusting Domain
Active Directory Users and computers tasks
a. Setup Allowed to Authenticate Permission on the domain controllers
(This will need to be completed on all domain controllers that are resolvable for the domain in DNS. This can also be scripted for larger environments. You can also limit the dns records resolvable to reduce the servers the permission needs to be applied to )
· Open ADUC by running DSA.msc
· Navigate to the domain controllers that need the permission applied.
· Setup the permission as below
(This is required for the trusted domain controllers to authenticate to the trusting domain controllers to query SPN’s and permission).
· Navigate to the FIM Synchronization Server and repeat the same permission
(This is required for the trusted domain controllers to authenticate to the FIM Synchronization Server).
· Navigate to the FIM Synchronization Server service account and repeat the same permission.
(This is required for PCNS on the trusted domain DC's complete to request a context change once the initial RPC bind is established which took me a while and a whole lot on netmon packets to figure out)
Group Policy Management Tasks
Open GPMC.msc on the domain controller
a. Open GPMC.MSC
b. Navigate to the “Default Domain Controllers Policy “ and right click and select edit.
c. Navigate to Computer Configuration,
d. Navigate to Windows Settings
e. Navigate to Security Settings
f. Navigate to User Rights Assignment
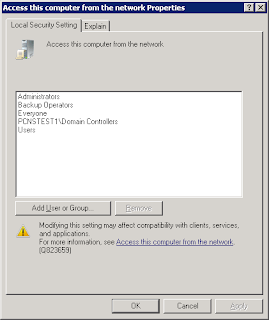
g. Navigate to the “Access this computer from the Network” Policy”
h. Add the Trusted domain Domain Controllers group to the list of accounts
a. Log into the FIM Synchronization Server as an Administrator
b. Open local computer group policy by running “gpedit.msc”
c. Navigate to Computer Configuration,
d. Navigate to Windows Settings
e. Navigate to Security Settings
f. Navigate to User Rights Assignment
g. Navigate to the “Access this computer from the Network” Policy”
h. Add the Trusted domain Domain Controllers group to the list of accounts
3. Trusted Domain
Group Policy Management Tasks
Open GPMC.msc on the domain controller
a. Open GPMC.MSC
b. Navigate to the “Default Domain Controllers Policy “ and right click and select edit.
c. Navigate to Computer Configuration,
d. Navigate to Administrative Templates
e. Navigate to System
f. Navigate to Kerberos
g. Navigate to the “Use forest search order” Policy”
h. Add the Trusting Domain to the list of Forests to Search for SPN’s. (This is needed for the trusted domain to be able to resolve SPN’s in the Trusting domain where the SPN for the FIM synchronization server service account is located– thanks Jorge for this one .. http://jorgequestforknowledge.wordpress.com/2011/09/14/kerberos-authentication-over-an-external-trust-is-it-possible-part-6).
Check the Service Configuration
Reset the user password
Verify that the password was successfully delivered
All working!!